Cisco 877 (800 serie) RFC 2684 (before 1483) multi-protocol over ATM, config Dommel CityConnect (Wan DHCP, ADSL2+)
Config I use for the Belgium provider Dommel with the Cityconnect ADSL2+ they offer.
- WAN IP: DHCP (ATM0.1 point-to-point)
- LAN Router IP: 10.10.10.1
- DHCP Range: 10.10.10.10 10.10.10.240
- DNS Server forwarding requests to OpenDNS
- NTP Server forwarding requests to 81.246.92.140 and 212.68.213.7 (be.pool.ntp.org ip's)
- Timezone Paris
- Incoming ACL: 101
- Outgoing ACL: 100
- SSH via WAN on port 822
- SNMP Private string: privateString
- SNMP Public string: publiekeString
- Logging previous 300 console commands
!* cisco-axelius.axelius.be.CiscoConfig
!* IP Address : 10.10.10.1
!* Community : privateString
!* Downloaded 21/03/2010 19:07:58 by SolarWinds Config Transfer Engine Version 5.5.0
!
! Last configuration change at 19:06:47 Paris Sun Mar 21 2010 by admin
! NVRAM config last updated at 19:06:53 Paris Sun Mar 21 2010 by admin
!
version 12.4
no service pad
service tcp-keepalives-in
service tcp-keepalives-out
service timestamps debug datetime msec localtime show-timezone
service timestamps log datetime msec localtime show-timezone
service password-encryption
service sequence-numbers
!
hostname cisco-axelius
!
boot-start-marker
boot-end-marker
!
logging buffered 51200 debugging
logging console critical
enable secret 5 ...
!
no aaa new-model
!
resource policy
!
clock timezone Paris 1
clock summer-time Paris date Mar 30 2003 2:00 Oct 26 2003 3:00
ip subnet-zero
ip cef
no ip dhcp use vrf connected
ip dhcp excluded-address 10.10.10.1 10.10.10.9
ip dhcp excluded-address 10.10.10.241 10.10.10.254
!
ip dhcp pool sdm-pool1
import all
network 10.10.10.0 255.255.255.0
default-router 10.10.10.1
dns-server 10.10.10.1
!
!
ip tcp synwait-time 10
no ip bootp server
ip domain name axelius.be
ip name-server 208.67.222.222
ip name-server 208.67.220.220
ip ssh time-out 60
ip ssh authentication-retries 5
!
!
crypto pki trustpoint TP-self-signed-4008809079
enrollment selfsigned
subject-name cn=IOS-Self-Signed-Certificate-4008809079
revocation-check none
rsakeypair TP-self-signed-4008809079
!
!
crypto pki certificate chain TP-self-signed-4008809079
certificate self-signed 01
30820250 ...
quit
username admin privilege 15 secret 5
archive
log config
logging enable
logging size 300
hidekeys
!
!
!
bridge irb
!
!
interface ATM0
description Fysieke ADSL (ATM) Interface
no ip address
no atm ilmi-keepalive
dsl operating-mode auto
!
interface ATM0.1 point-to-point
description ATM Routed Bridge Encapsulation (RBE) Subinterface t.b.v. Internet
ip address dhcp
ip access-group 101 in
ip nat outside
ip virtual-reassembly
no snmp trap link-status
atm route-bridged ip
pvc 8/35
encapsulation aal5snap
protocol ip inarp
!
!
interface FastEthernet0
!
interface FastEthernet1
!
interface FastEthernet2
!
interface FastEthernet3
!
interface Vlan1
description $ETH-SW-LAUNCH$$INTF-INFO-HWIC 4ESW$$ES_LAN$$FW_INSIDE$
ip address 10.10.10.1 255.255.255.0
ip access-group 100 in
ip nat inside
no ip virtual-reassembly
!
interface Dialer0
no ip address
!
ip classless
!
ip http server
ip http authentication local
ip http secure-server
ip http timeout-policy idle 60 life 86400 requests 10000
ip nat inside source list 1 interface ATM0.1 overload
ip nat inside source static tcp 10.10.10.1 22 interface Dialer0 822
ip dns server
!
logging trap debugging
access-list 1 remark INSIDE_IF=Vlan1
access-list 1 remark SDM_ACL Category=2
access-list 1 permit 10.10.10.0 0.0.0.255
access-list 100 remark CCP_ACL Category=17
access-list 100 deny ip host 255.255.255.255 any
access-list 100 deny ip 127.0.0.0 0.255.255.255 any
access-list 100 permit ip any any
access-list 101 permit tcp any any established
access-list 101 permit udp host 212.68.213.7 eq ntp any eq ntp
access-list 101 permit udp host 81.246.92.140 eq ntp any eq ntp
access-list 101 permit udp host 208.67.220.220 eq domain any
access-list 101 permit udp host 208.67.222.222 eq domain any
access-list 101 permit tcp any any eq 822
access-list 101 permit icmp any any administratively-prohibited
access-list 101 permit icmp any any echo
access-list 101 permit icmp any any echo-reply
access-list 101 permit icmp any any time-exceeded
access-list 101 permit icmp any any traceroute
access-list 101 permit icmp any any unreachable
access-list 101 permit udp any eq bootps any eq bootpc
access-list 101 deny ip any any
snmp-server community privateString RW
snmp-server community publiekeString RO
snmp-server location Hasselt
snmp-server contact GregoryBE
!
control-plane
!
banner login Authorized access only!
Gretech Configured router. Unauthorized access will be logged.
!
line con 0
login local
no modem enable
transport output telnet
line aux 0
login local
transport output telnet
line vty 0 4
privilege level 15
login local
transport input telnet ssh
!
scheduler max-task-time 5000
scheduler allocate 4000 1000
scheduler interval 500
ntp clock-period 17179862
ntp master
ntp server 81.246.92.140 prefer
ntp server 212.68.213.7
end
Links:
http://www.cisco.com/en/US/tech/tk175/tk15/technologies_configuration_example09186a008071a5d0.shtml
http://forums.overclockers.com.au/showthread.php?t=460519
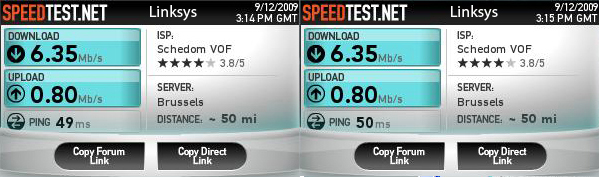
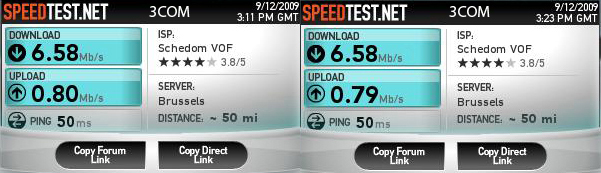
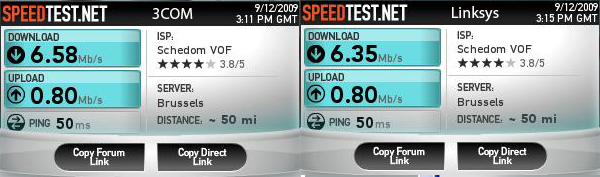
Linksys/3Com ADSL modem speed test
Just a little test I performed: Two different ADSL modems on the same ADSL2+ Line, same cable, same connectors...
3COM: OfficeConnect ADSL Wireless 108 Mbps 11g Firewall Router
Linksys: WAG200G
(Did the test serveral time to make sure the results are correct.) I should have taken note of the noise and margin values, will do that in future tests...
Flashing DDWRT (on WRT54GL)
Recently I was talking with a friend (Jones) about DD-WRT and Tomato, he told me that an hard reset is always required before and after flashing a firmware, something I didn't know. I always just flashed the firmware...
So basically how to flash a WRT54GL with the original Linksys firmware on it (using GUI):
- Download Micro or Mini to start with,
If you want to install another DDWRT version, afterwards also download it (STANDARD, VOIP, or VPN versions)
DDWRT Firmwares - Hard reset (original Linksys firmware)
- Upgrade to Micro or Mini
- The Waiting...
- Hard reset
- Upgrade to the STANDARD, VOIP, or VPN versions.
- The Waiting...
- Hard reset
What is a Hard reset (30/30/30 reset):
- Hold down the reset button for 30 seconds (with the router powered on)
- Still holding it, pull the power cord for 30 seconds.
- Still holding it, plug the router back in and continue to hold the reset button for 30 more seconds.
(When the hard reset is performed correctly, you will be asked to change your password when you login to the webgui)
The Waiting:
After you flash the firmware, and before you do the hard reset, the router will be building some nvram settings. YOU MUST WAIT FOR THIS TO FINISH PRIOR TO DOING ANYTHING WITH THE ROUTER INCLUDING A HARD RESET. Usually, you can tell when this process is completed by the WAN light coming on, but it does take several minutes. Go have a beer. There are starting to be more and more people who BRICK their routers by not waiting until the nvram is rebuilt, PRIOR to doing a hard reset. YOU NEED TO WAIT!
The reason for the hard resets:
You want to flash to a "clear" nvram. This helps to prevent problems. That is the reason the chip is being cleared prior to flashing. Old values can corrupt things. So can failing to power cycle. Without doing a hard reset it is possible that your WRT54GL will get slow.
Links:
Linksys WRT54GL
Peacock Thread-FAQ: EVERYTHING you NEED to know! Really!! (very handy)
Flashing Your Router with DD-WRT Firmware